By adaptive - August 26th, 2014
As cyber attacks continue to rise, how should your corporation ensure its use of social media networks is secure?
Using social media in a corporate environment means paying particular attention to security. However, the latest Kaspersky Labs security report illustrates that there is much more that needs to be done in order to secure social media networks.
The survey shows that communication via social networks is one of the most popular activities on the Internet. Overall, using social media sites was the third most popular activity after checking email and reading articles or books, and it was even more popular on mobile devices – ranking second.
People are often careless with what information they share over social media networks. While using social media networks, every tenth participant discusses private information on social media networks with strangers, but only 18% think they reveal more personal information than they should on social networks. In general, 15% share information online that they would not disclose in the real life.
Also, 78% of the respondents do not think they are of any interest to cybercriminals or are unsure about this issue. However, cybercriminals are always lurking and often look through social networks searching for information inadvertently left by the user. Information such as an email address can be used to help an attacker break an account password or identify a person’s location. In turn, access to a user’s account can give cybercriminals the opportunity to send malicious links and files to the victim’s friends, stealing their personal data as well.
For all corporations, securing the data that flows across their networks is of paramount importance. With the continued rise of remote working and BYOD, a comprehensive security policy that governs how social media networks should be used is critical to develop and keep up-to-date.
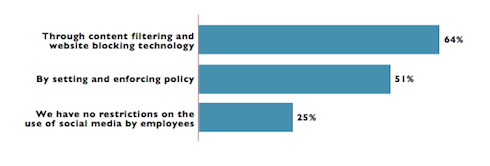
Many corporations simply limit the access that their employees have to the social media networks, as the last Frost & Sullivan Global Information Security Workforce study revealed:
“The most prominent means to limit access to social media is by using content filtering and website blocking technologies. The prominence of these technologies is greater with larger companies than small. Not surprisingly, higher proportions of medium, large, and very large companies surveyed use this technology for social media access control than small companies.
“Also as expected, survey respondents in the banking, insurance, and finance verticals expressed greater use (82%) of these technologies than any other vertical. Respondents in the education vertical are the most permissive in social media access; 59% state their organizations have no social media restrictions.”
Restricting access
The level of restriction your corporation places on social media access need to be balanced with a robust attitude to security. The news headlines are regularly filled with stories of cyber attacks – many of which take place across the social media networks. Completely banning the use of social media outside of your businesses marketing channels for instance is often not a practical proposition.
Corporations now understand that their social media advocates are not just customers, but also their own employees. Dell for instance established their Social Media and Community (SMaC) and their Social Media and Community Universityin 2010 to ensure all of their employees understood not only the power of social media, but also how to use it responsibly and securely.
DachisGroup also comments: “Employee advocacy is simply too powerful of a tool for brands to pass up. Companies like Lululemon and others have mastered offline processes to create the conditions of empathy, understanding, and expertise that make employee advocacy work. The next step is to translate those tactics online and into social channels. But without the right foundation in place — for both employee advocates and those responsible for program execution — that value remains untapped and enclosed within the walls of your organization.”
Kaspersky recommend these components should be included in your corporation’s social media security policy:
- Use strong passwords for accounts and disable the auto-complete function, especially if logging in from your smartphone or tablet.
- Restrict the amount of information shared on any networks. Divide ‘friends’ into groups so that information can be shared with only those really trusted.
- Do not download files, and do not follow suspicious links from unknown senders.
- Before entering credentials, make sure it is not a fake page created in order to obtain usernames and passwords.
- Try to use a secure connection if possible, and do not enter login and password when connecting to a hotspot over public Wi-Fi.
- Make sure the device used to enter a social network is well protected: use a password to access the device and a reliable security solution.
What is clear is that corporations simply can’t throw up firewalls to protect their enterprises from cyber attack, as they need to allow employees access to social media networks for them to remain effective. However, a well-defined social media policy that clearly sets out the security protocol that should be followed is essential for all corporations. The use of BYOD and remote access technologies are creating an uncertain and potentially damaging security environment, but one that can be mitigated with sensible security precautions.
Image Source: Freedigitalphotos.net
Next Reads
November 2014, New York
The Social Media for Customer Service Summit is your one-stop-shop for all the latest social media insight and best practice. It gives you a 360 degree look into building, operationalizing and initiating a successful social media strategy at your company
Brochure Programme