US tackles cyber security threat from surging renewables
US scientists are testing layers of cyber defences from component level and designing new grid topology and control systems to counter the threats posed by rising renewable energy capacity.

Related Articles
In January, the US National Renewable Energy Laboratory (NREL) launched a new Cybersecurity Program Office (CPO) to tackle the impact of rising renewable energy capacity and distributed energy systems on grid security.
Launched in January, the CPO will study how communication networks and individual components, such as inverters and supervisory control and data acquisition (SCADA) systems, impact power system security.
Solar capacity is rising fast and concerns over cyber attacks are growing. Solar inverters have been identified as a key cyber risk and the expanding geographical spread of solar installations increases the challenge. The US Department of Energy (DOE) is funding research into cutting-edge inverter software and hardware designed to minimise the threat.
Global digitalisation and surging renewable energy build are raising cyber security risks, Tony Cole, Chief Technology Officer at cyber security company Attivo Networks, told Reuters Events.
The COVID-19 pandemic has accelerated digitalisation and President Joe Biden's plan to rapidly increase renewable energy capacity puts further pressure on grid security, he said.
The US must add "hundreds of gigawatts" of renewable energy over the next four years to meet Biden's target of a zero-carbon power sector by 2035, U.S. Secretary of Energy Jennifer Granholm said March 3.
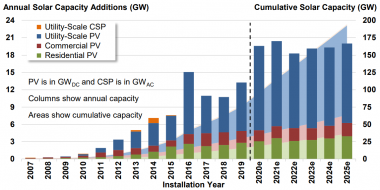
US annual solar installation forecast
(Click image to enlarge)
Source: Berkeley Lab (November 2020), IREC, Wood Mackenzie
More devices are being added to communication networks, creating more vulnerability points. Distributed energy, storage, smart grids, and broader integration with Wi-Fi, satellite imagery and 5G all create challenges for system security.
Thus far, solar inverters have been identified as a theoretical cyber risk, but it is only a matter of time before a real attack occurs, Thomas Edgar, Cyber Security Research Scientist, Secure Cyber Systems at the Pacific Northwest National Laboratory (PNNL), said.
New power sources and communication devices will increase the complexity of the grid and current security approaches will be insufficient, he said.
System view
NREL's new cyber security office will evaluate the dynamic interactions between communication systems and energy systems.
The CPO team will develop metrics for evaluating security and conduct system simulation, risk analysis and impact assessments, Office Director Jonathan White told Reuters Events.
The team will study “millions of devices, distributed architectures, and their resulting connections" under realistic market scenarios, using its Advanced Research on Integrated Energy Systems (ARIES) platform, he said.
The platform allows it to understand the implications of "many different types of threats,” White said.
Redundancy must be built into the critical network and system infrastructure to maintain system integrity in the event of an attack.
Key challenges include the growing communication requirements across the sector and rising number of solar and wind installations, which will require plant monitoring and supply chain testing, White said.
Wind and solar plants can include hundreds of independent devices from a diverse set of technology providers.
Each device and sensor can create a tripwire, providing "hundreds of ways to detect and stop malicious intents," he said.
Controlling costs
Wind and solar operators must comply with cyber security standards set out under the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP). States such as California and Hawaii have introduced further guidance and more specific measures for renewable energy operators are in the pipeline. Industry groups and national laboratories are working with state officials on new standards that could be used to "validate and certify the cyber security posture of distributed energy devices, such as PV inverters, before they enter the market," White said.
Enhanced cyber security measures will need to be rolled out at minimum cost to maintain the competitiveness of PV plants, White noted. The cost of measures such as supply chain testing must not be placed solely on the asset owner, he said.
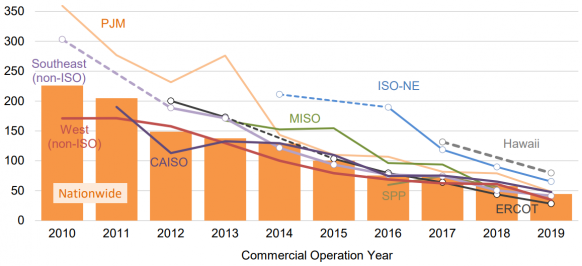
Levelised cost of US utility-scale solar by market
(Click image to enlarge)
Source: Berkeley Lab, November 2020
The wide range of component ages in solar and wind plants creates additional challenges for security, Cole said. Older models may not respond to security updates while new apps and hardware that are quickly brought to market can have "few security controls in place," he said.
NREL’s CPO team will also collaborate with solar companies and develop workforce training, White said. Employee access and password security remain key sources of cyber intrusion. Tactics used by attackers include open-source reconnaissance and spear-phishing emails from compromised legitimate accounts.
Smarter grids
Grid level measures will also be required to accommodate the widening range of power generation and storage devices and communication technologies.
PNNL is studying innovative forecasting approaches that can respond to adverse market events like cyber attacks and improve the resilience of the power grid, Edgar said.
Using information from layers of devices, adaptive control systems could make predictive decisions in real-time that manoeuvre around fault conditions, he said.
PNNL is also investigating a redesign of grid topology and new sensoring configurations. The laboratory is studying the key concepts of resiliency and aims to investigate "groups of microgrids within a distribution system or across geographically-close distribution systems,” Edgar said.
New sensor types and additional switching controls could be used across the distribution system, he said.
There is still a lack of harmony “between the rapid patching, always-evolving software world and the long-life cycle, methodical change management of critical infrastructure,” Edgar noted.
The evolving threat of cyber attacks means that security measures must continue to be enhanced and updated throughout the operations phase. More should be done to roll out best practices across the power industry, even down to basic measures such as not using default passwords and enforcing basic network segmentation, Edgar said.
“It is often dependent on the utility and how they are organizationally structured and manage their risks,” he said.
Reporting by Neil Ford
Editing by Robin Sayles